Introduction
In the ever-evolving landscape of web security, new measures are constantly being developed to protect digital assets from unwanted traffic, automated bots, and malicious attacks. One such measure that has recently caught the attention of the cybersecurity community is Vercel's introduction of the "Attack Mode". This security feature, designed to thwart attacks and manage traffic, has sparked a debate on its effectiveness and real-world implications.
What is Vercel?
Vercel is a cloud platform for static sites and Serverless Functions that enables developers to host JAMstack websites with ease. It's known for its incredible performance, scalability, and ease of use, making it a popular choice for front-end developers.
The Attack Mode
Vercel's Attack Mode is a security measure aimed at protecting websites from excessive and potentially malicious traffic. When activated, it presents a challenge-response mechanism to users, ostensibly to differentiate between human users and automated bots. However, an in-depth examination reveals that this challenge, rather than being a robust defense, can be easily decoded, recreated, and bypassed.
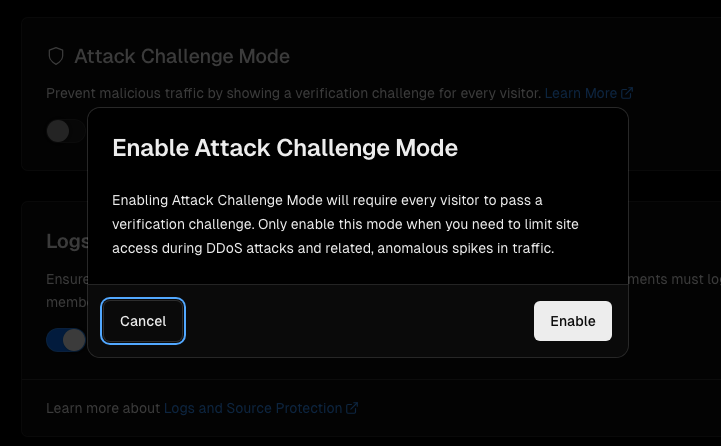
Understanding and Solving the Challenge
The challenge mechanism under Attack Mode sends users a 429 status code, indicating throttling, and includes a challenge within the response HTML. This challenge, which also comes with a unique token (x-vercel-challenge-token), requires a solution to be submitted via a POST request to allow access.
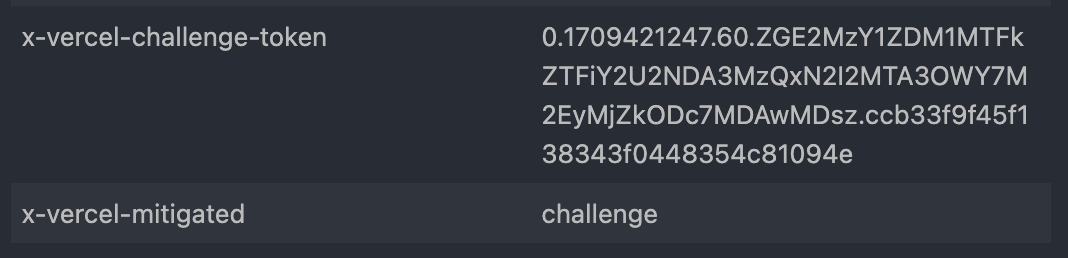
However, as detailed in our GitHub repository, solving this challenge is far from a herculean task. The repository provides a comprehensive guide on interpreting, solving, and even deobfuscating the challenge. The process involves understanding the challenge from the response HTML, computing the solution using the provided token, and submitting the solution. Our deobfuscation resources further illuminate the simplicity of bypassing this security measure, raising questions about its efficacy.
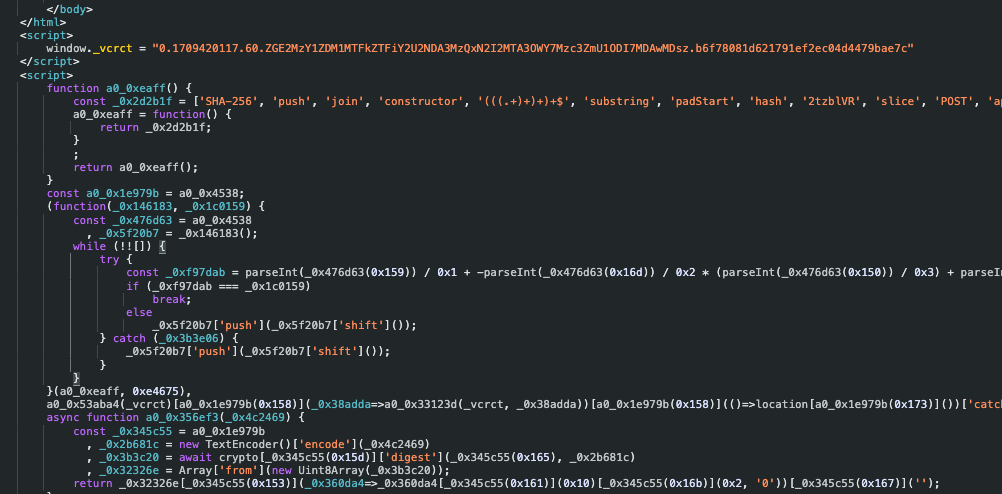
Is It Stopping Bots?
The short answer: no. Despite its intentions, Vercel's Attack Mode does little to deter determined attackers or sophisticated bots. The mechanism's reliance on a solvable challenge means that any bot equipped with the right scripts can easily gain access. This reality underscores a fundamental issue in web security measures that rely on challenges easily decoded by machines.
Two Key Situations Unpacked
- Absence of Automated Browser Checks: In scenarios where there's no mechanism to differentiate between automated browsers and human users, the computations proceed as though they're being executed by a legitimate user. This oversight allows bots to interact with web resources without encountering any form of verification or challenge, undermining the security posture significantly.
- Requests-Based Bot Attempts: For bots that operate on a request-based model, circumventing the challenge becomes trivial. Such bots can execute three simple JavaScript functions to solve the challenge, subsequently generating valid headers. This capability demonstrates a significant flaw in the challenge-response mechanism, as it fails to provide a robust barrier against automated access attempts.
Conclusion
While Vercel's Attack Mode might seem like a step forward in the fight against web threats, its effectiveness is questionable. The ease with which the challenge can be solved and bypassed not only undermines its purpose but also highlights the need for more innovative and foolproof security measures. As cybersecurity professionals and enthusiasts continue to reverse-engineer and outmaneuver such defenses, the conversation around digital protection becomes ever more critical. For those interested in the technical breakdown of solving Vercel's Attack Mode, our GitHub repository provides a deep dive into the challenge and its shortcomings.
Member discussion: